US Defense Advanced Research Projects Agency’s SHIELD project began earlier this year with multimillion-dollar awards to Northrop Grumman Systems ($12.3 million), SRI International ($6.8 million), and Charles Stark Draper Laboratory ($4.1 million).
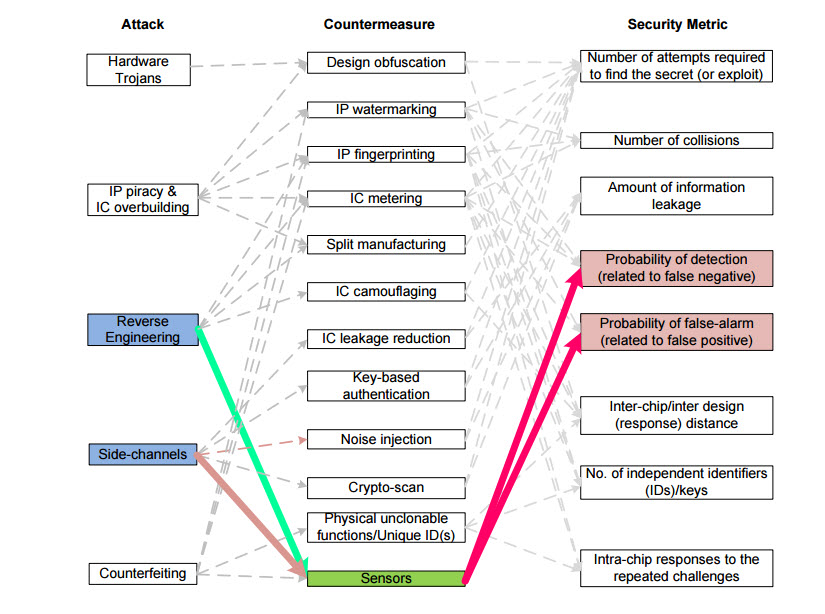
There are five types of hardware attacks DARPA is trying to manage: 1) Hardware Trojans, 2) IP piracy & IC overbuilding, 3) reverse engineering, 4) side-channels, and 5) counterfeiting. See “Attacks,” “Countermeasures,” and “Security Metrics” below:
From Design, Manufacturing and Testing, to Packaging and Distribution
As much of the world’s electronics is manufactured in China, the fear has been that Chinese engineers are surreptitiously adding “listening devices” or fake or faulty parts to consumer, business, and military weapon systems. According to reports, counterfeit hardware has been flooding supply chains for years. While China gets the most blame, some US manufacturers have been caught red-handed.
SHIELD is developing miniature components, called dielets, that can be attached to electronic parts during manufacturing. The dielets are being designed with encryption capabilities and sensors to detect tampering. Dielets would sense exposure to light that might occur if hardware is opened up and tampered with. The dielets are powered by external sources so as not to interfere with the electronics they are protecting.
The program seeks to manufacture dielets at less than a penny each and handheld RFID devices or smartphones will be used to scan large shipments in seconds, communicating with sensors to see if tampering has occurred. Another goal of the program is to ensure that the system identifies counterfeit parts at all points along the supply chain.
For more information see a paper by ACES Lab “Shielding and Securing Integrated Circuits with Sensors.”