Since Cyber War is a covert activity we can gain insight into the resources being marshaled by nation states by looking at the way they prepare for the Olympic Games. Russian and Chinese Olympic organizations, for example, search their populations for the most talented children, often removing them from their homes, and fast track them through intensive training programs with the goal being to bring home gold medals every four years, regardless of the human and financial cost. Arguably the stakes in Cyber War are much higher; we can imagine teams of young geniuses with computer programming talent being trained all around the world to infiltrate computer systems for economic and military gain.
The US Defense Department, in response to this growing threat, is in the process of dramatically boosting cyber security by recruiting what it refers to as Cyber Warriors; this recruiting effort is being called the Manhattan Project of the current college age generation.
A recent dramatic example of Cyber War was the effort to spy on and sabotage the Iranian Nuclear Program’s computer systems in 2010. Carried out through the infection of computer systems by a “worm” called “Stuxnet”. Stuxnet spread from Microsoft Windows to Siemens Industrial Software and equipment. The worm delivered a payload designed to monitor and subvert supervisory control and data acquisition systems and infect Programmable Logic Circuits (PLCs). The target was undoubtedly the uranium enrichment infrastructure in Iran which was reportedly set back months, if not years. Ironically this effort was believed to be a part of a US/Israeli operation dubbed “Operation Olympic Games”. Shortly after Stuxnet it is believed Iranian hackers began attacking US banks and other key sites in retaliation.
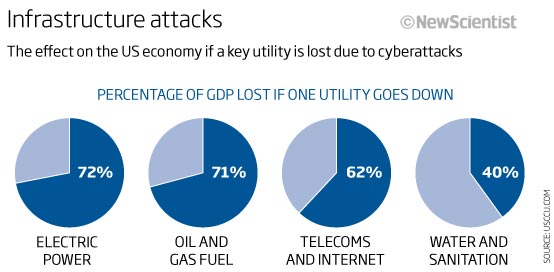
The US is seeking to protect itself from what it calls a “Cyber-Pearl Harbor” which would be a surprise attack on a vital US computer system that runs critical infrastructure: electrical grids, nuclear power stations, financial markets, etc.
Reportedly US government agencies, defense contractors, technology firms, universities, banks, utilities, email accounts and companies like Google, Facebook, and Lockheed Martin and many others have been compromised.
Craig Chambers of RandomUserID has worked on numerous cyber security systems and sums up the issues:
- Countries cannot disconnect from the Internet.
- Geographic borders are meaningless on the Internet. Computers are routinely hijacked by the millions across many countries.
- Hijacked computers become attack platforms or relays helping to conceal the identity of the attackers.
- Attackers often use a tech platforms and relays located in countries where law enforcement does not cooperate with outside countries.
- It is difficult to identify the IP address of an individual computer making it difficult to identify perpetrators
- ISPs do not verify the identity of new account users making it easier for attackers to create thousands of bogus accounts.
- Converting the Internet to Internet Protocol Version 6 (IPv6) in which each computer and device would have a unique identity would help flush out hackers by keeping track of the number of attacks launched from specific computer and devices. However converting to IPv6 is complicated, expensive and will take years.
- Western countries are based on the rule of law where the expectation is that if people break the law they can be punished; where cyber war is being waged in countries not committed to the rule of law it is exceedingly difficult to prosecute hackers.
According to Chambers, Cyber War is now affecting the profitability of private industry as they are beginning to hire large numbers of security engineers and technicians. But solving the problem of Cyber War through a new and ongoing cyber arms race is perhaps not the way to go. Finding a way to bring countries into a legal structure of treaties where intellectual property is protected and theft whether by individuals, companies or governments is aggressively prosecuted may be the only reasonable and effective solution.
Stay tuned as we will go into more detail on the technology used in Cyber War in future posts!
Related Posts: